The Ultimate Guide to Multi-factor authentication
2025 edition
Analyst reports

Gartner on MFA & Malware
AI to halve time needed for account takeover by 2027
Wed, 19th Mar 2025

Gartner on MFA & Data Protection
Entrust launches AI identity tool to tackle USD $112bn ...
Wed, 22nd Jan 2025

Gartner Peer Insights on MFA & Firewalls
WatchGuard wins TrustRadius awards for cybersecurity
Fri, 8th Nov 2024

Forrester Wave on MFA & IoT
ColorTokens acquires PureID to enhance Xshield capabili...
Tue, 17th Sep 2024

Gartner on MFA & PAM
Claroty reveals remote access risks in OT environments ...
Wed, 11th Sep 2024
Expert columns

By Kon Poptodorov of LexisNexis Risk Solutions
Strengthening cyber resilience in superannuation
Yesterday

By Horatiu Petrescu of Aura Information Security
Privacy Week: Sensitive information stored online can h...
This month

By Robert Vinokurov of Dell Technologies
It’s the end of passwords as we know it
This month

By Mary Attard of Accenture
A future with no passwords: Why passwordless authentica...
This month

By Robin Long of Rapid7
World Password Day reminds us: It’s time to rethink acc...
Last month
Interviews

Discussing Ransomware
Google Threat Intelligence explains China’s evolving cy...
Last month

Discussing Phishing
Exclusive: Yubico pushes for wider protection under Aus...
Mon, 31st Mar 2025

Discussing Firewalls
Exclusive: SailPoint's Chris Gossett discusses keeping ...
Wed, 27th Nov 2024

Discussing Threat intelligence
Exclusive: Rapid7's Craig Adams discusses cybersecurity...
Tue, 26th Nov 2024

Discussing Software Updates
Exclusive: AUS 3C report reveals how different generati...
Tue, 1st Oct 2024
More expert columns

By Victoria Boryaeva of Pulseway
Essential Eight: Full cyber resilience through complian...
Last month

By Rakesh Prabhakar of Zoho
How can small and medium businesses safeguard against r...
Last month

By William Oh of BlueVoyant
DBS & Bank of China Singapore hit by cyberattack
Last month

By Chris Fisher of Vectra AI
Outpacing AI-Driven cyber attacks: Strategies for moder...
Last month
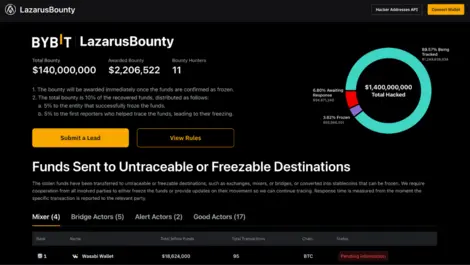
By Janine Grainger of Easy Crypto
Bybit: when hackers target people, not systems
Mon, 24th Mar 2025

By Johan Fantenberg of Ping Identity
How A Passwordless Future Can Become A Reality
Thu, 30th Jan 2025
Recent news
About Enterprise security
Cisco Duo launches identity service to tackle AI cyber ...
2 days ago

About Firewalls
Cisco unveils Duo IAM to strengthen identity-based secu...
3 days ago

About Data Protection
Synology unveils cloud surveillance service with easy d...
Last week

About Fintech
Fintech sector faces mounting third-party security brea...
Last week

About Firewalls
SEO poisoning attack diverts wages using fake payroll w...
Last week
More news

About Ransomware
Ransomware attacks on industrial targets surge, AI tact...
Last week

About Enterprise security
Yubico expands YubiKey services to 175 countries global...
Last week

About Software-as-a-Service
AI tools expose sensitive data at 99% of organisations
Last week

About Spam
Phishing attacks become harder to spot as hackers adapt...
This month

About Software-as-a-Service
Cybersecurity spend to surpass $200B as risks surge
This month
Even more news

About Firewalls
Hackers target FTP servers with weak passwords, study f...
This month

About Ransomware
Scattered Spider exploited UK retailer service desks
This month

About Endpoint Protection
AI arms race fuels surge in cybercrime & deepfake scams
This month

About Cloud Services
Businesses intensify efforts to secure data in cloud co...
This month

About Surveillance
ANZ to launch password-less web banking with enhanced s...
This month
Job moves

Move at Palo Alto Networks
WatchGuard CEO Prakash Panjwani steps down as Vats Sriv...
This month

Move at Yubico
Yubico Expands APJ Sales Team with New Executives in Si...
Wed, 4th Oct 2023
.webp)
Move at Samsung
HoJin Kim appointed as WatchGuard's SVP & Chief Revenue...
Thu, 6th Apr 2023

Move at Yubico
Yubico Announces Exciting Leadership Changes
Thu, 16th Feb 2023

Move at Okta
Exclusive: Okta’s new GM shares its APAC strategy
Fri, 19th Oct 2018
Other guides
You can read other related guides from Cybersecurity, Advanced Persistent Threat Protection, Email Security, Artificial Intelligence, and Phishing.
Powered by